How to Build A Computer Security Incident Response Plan (CSIRP) That Works?
The cybersecurity threat is increasing exponentially, driven by digital transformation and cloud migration.
If you store, process or handle data, you are at risk for cyber threats.
All businesses, irrespective of their size, location and industry, have one thing in common: the networks and systems are under almost continual cyber threat.
In fact, it is virtually inevitable that your business will suffer a security breach at some point.
A successful cyber-attack can devastate even the most resilient of businesses. It can often result in financial loss, reputational damage and legal consequences.
According to a recent report, over 3,800 data breaches were reported in the first half of 2019, exposing over 4.1 billion records.
2019 Data Breach Highlights
- USD 3.92 million – Global average cost of a data breach
- USD 150 – Cost per lost record
- USD 8.19 million – Average cost of a data breach in the USA
- 279 days – Time to identify and contain a breach
- 25,575 records – Average size of a breach
Even though data breaches are inevitable, proper planning and preparation for these events can significantly reduce the damage.
ALSO READ | 2020 Insider Data Breach Survey Report
Having a clear, specific, and current Computer Security Incident Response Plan (CSIRP) has become a necessity.
According to the Ponemon Institute, having a CSIRP in place is second to a strong cybersecurity posture reducing the damage of a data breach.
What is Computer Security Incident Response Plan (CSIRP)?

A CSIRP is the guide map that precisely explains how to respond to the most probable security threats and associated incidents.
As a cornerstone of your defense against cybercriminals, malware, insider threats, and a host of other risks, a CSIRP can help reduce the cost and mitigate the severity of breaches.
It specifies all respondents’ roles and responsibilities, establishes authority for making significant decisions, and defines communication flows and notification procedures.
With a CSIRP, the incident response team can figure out what to do without wasting valuable time and resources during a security incident. This, in turn, can significantly decrease the damage caused by a security breach.
At this juncture, we bring you some best practices to develop a Computer Security Incident Response Plan (CSIRP) for your business.
ALSO READ | U.S. Data Breaches and Exposed Records 2019
How to Develop a Computer Security Incident Response Plan (CSIRP)?
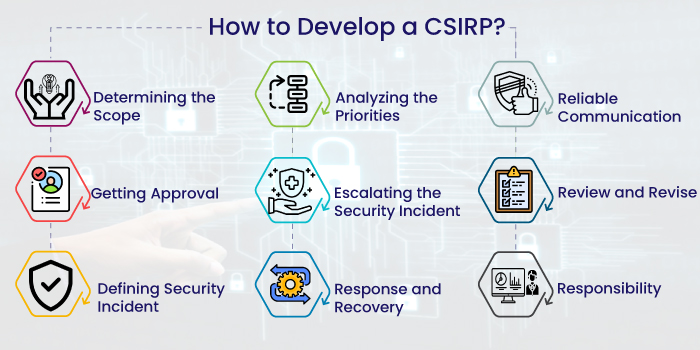
The incident response plan will be unique to every organization. However, in general, the approach and structure of the CSIRP will be the same regardless of the business type, size and location.
1) Determining the Scope
Before drafting a CSIRP, it’s crucial to determine the scope of the plan. The scope of the plan can cover a service, a department or a whole organization. And, of course, the complexity of the planning task increasing with the size of the scope.
If this is your first try, then it is advised to start with your organization’s critical services and essential functions.
2) Getting Approval
Gaining approval for the CSIRP is the crucial step. It’s imperative to convey the urgency of the task to concerned management to allocate funds and get the approval for CSIRP. One should get approval even before committing the time and resources to do this. If the scope of the CSIRP is just one service, you need to gain approval from only the manager of that service.
3) Defining Security Incident
To respond to any security incident, you must have a system or a tool to indicate that an incident has occurred. This type of resource should be designed into your systems for capturing and logging information to be analyzed to know an event occurred.
Then, define what a security incident is to your organization, whether it be malware, a DDoS attack, or unauthorized access to files. Generally, anything that disrupts the services or systems defined in the scope can be considered as a security event.
Document all the types of incidents and responses while indicating the priority in responding to events based on their criticality.
4) Analyzing the Priorities
When many security incidents coincide, you should be prepared to determine the order of operations and respond to the most critical one first. For it, you need to determine the systems and components that are most critical for your business functions and those with the least preference.
Typically, you can categorize the security events by their severity. You can also consider the amount of time you can afford for the systems to be down before actual damage is caused.
Moreover, you should develop a method or technique to analyze the security incident to know if other co-occurring events are related to the same root cause.
Ensure to document the priorities and processes, and train the concerned team members.
5) Escalating the Security Incident
Now comes the task of determining what issue qualifies as a security incident. For instance, the IT department can simply handle a malware infection on a single computer by unplugging the system from the network. There is no need to escalate the incident to senior management. However, if a DNS server is under attack, it becomes an issue for the whole organization.
You need to determine what qualifies as a security incident and establish the criteria for escalating it to senior management.
After establishing the criteria for escalating the security incident, you should determine the procedure to respond. A response plan should include the procedure for analyzing the incident, who will analyze the incident, what software tools you will use to evaluate the incident.
Ensure to train the concerned employees on the analysis procedure.
ALSO READ | Cyber Security Incident Response Service Provider in USA
6) Response and Recovery
Hopefully, your organization has already established protocols on when to implement a Business Continuity Plan (BCP) and a Disaster Recovery Plan (DRP). You should have these procedures in place when the security incident qualifies as a disaster. Regardless of the severity of the incident, the concerned security team should have a plan to deal with it.
To create a Response and Recovery Plan, you need to consider the following things
- Developing a template for an incident report to make documentation consistent and straightforward, and easy to correlate with other incident documentation
- Procedure for damage control and continuity of critical services
- Tools, software and skills required to resolve the incident
- Internal and external entities required to coordinate recovery efforts
- Procedure to restore to full functionality or normal operations once the incident has passed
- An order to the restoration of services based on their priority
- Method of reporting your resolution status to all stakeholders
7) Reliable Communication
During a security incident, you must communicate what is going on with all the stakeholders so they are kept in the loop and know how long the incident may last. It’s imperative to keep all the stakeholders informed throughout the recovery process.
For this, you should assign a dedicated team ahead of time.
You should develop procedures and plans to communicate through each phase of the incident response in a reliable and timely manner.
The phases include
- Determining the security incident
- Escalating the incident to management
- Prioritizing your response
- Analyzing the incident
- Recovery to normal operations
8) Review and Revise
A review of the security incident will help you in the next revision of your incident response plan. It will also help take immediate steps to resolve any vulnerabilities in your systems, policies, or procedures.
You need to identify the root cause of what happened to continuously improve your detection and protection processes. You should also get to know what went wrong with your plan and process.
9) Responsibility
Now is the time to reevaluate who is responsible for what. You should explicitly define who is accountable for detecting security incidents, who escalates the events, and who is responsible for resolving them.
ALSO READ | Why Cybersecurity is Important for Small Businesses?
In Conclusion
Regardless of the nature of your business, the structure of the CSIRP will be the same. However, it should contain processes and specific procedures that abide by the scope determined during the preparation phase. A good CSIRP will explicitly define the resources needed to implement the plan backed by managed support.
While the necessary components of a CSIRP are simple, developing an effective plan requires balancing usability and thoroughness.
Owing to the rapidly evolving threat landscape, it is not feasible to craft a plan to address every potential attack. Even the organizations do not encourage a document that detailed and complex. Try to build flexible guidelines that can be applied quickly and easily to any type of incident.
Do You Have A Computer Security Incident Response Plan (CSIRP)? If Not, It’s Time To Make One.
Stealthlabs Is Here to Help!
Stealthlabs is a US-based Cyber Security Consulting Service Provider with strong domain expertise in evaluating your current security posture, including your plans and procedures. Our Incident Management Services Portfolio comprises of Incident Response, Incident Evaluation, Incident Retainer, and Compromise Assessment.

