Security Firm Fortinet Suffers Cyberattack, Almost 500,000 VPN Account Credentials Leaked
Cybercriminals are leaving no stone unturned in honing their hacking skills. Even the cybersecurity firms that are supposed to address the increasing threat of cyberattacks are succumbing to the nefarious plans of malicious actors all the time.
Recently, network security solutions provider Fortinet confirmed that it had suffered a massive credential data breach. The malicious actor has allegedly extracted VPN account login names and passwords of 87,000 FortiGate SSL-VPN devices.
“Fortinet has become aware that a malicious actor has recently disclosed SSL-VPN access information to 87,000 FortiGate SSL-VPN devices,” said the California-based security firm.
FortiGate is Fortinet’s flagship enterprise firewall platform. It provides a broad array of next-generation security and networking functions.
Also Read: REvil’s Faux Pas Thwarts Massive Ransomware Attack
Fortnite data leak on RAMP hacking forum
According to Fortinet, the hackers elicited the access information of VPN accounts from the systems that remained unpatched against a two-year-old vulnerability, ‘CVE-2018-13379’.
“These credentials were obtained from systems that remained unpatched against FG-IR-18-384 / CVE-2018-13379 at the time of the actor’s scan,” the company informed.
CVE-2018-13379 is a path traversal vulnerability in the FortiOS SSL VPN web portal. It enables unauthorized actors to download FortiOS system files, including the session file storing usernames and passwords in plaintext.
The flaw emerged as one of the most exploited security vulnerabilities in 2020 and 2021, according to a joint advisory issued by the FBI, CISA, ACSC, and NSCS.
Though the company patched the vulnerability in May 2019, multiple threat actors have been exploiting the security loophole to deploy an array of malicious payloads on unpatched devices.
This time, the users who patched that vulnerability but failed to reset the passwords have fallen victim.
Also Read: LockBit Hackers Exploit Accenture to Compromises an Airliner!
Without further ado, Fortinet directed all its customers to upgrade their VPN devices and perform user password reset.
“We are reiterating that, if at any time your organization was running any of the affected versions, even if you have upgraded your devices, you must also perform the recommended user password reset the following upgrade,” instructed Fortinet.
“Otherwise, you may remain vulnerable post-upgrade if your users’ credentials were previously compromised.”
“Please note that a password reset following upgrade is critical to protecting against this vulnerability, in case credentials have already been compromised,” reiterated Fortinet.
The affected products in the attack include FortiOS 6.0 – 6.0.0 to 6.0.4, FortiOS 5.6 – 5.6.3 to 5.6.7, and FortiOS 5.4 – 5.4.6 to 5.4.12.
Fortinet recommended all the affected customers to immediately disable all VPNs, upgrade the devices to FortiOS 5.4.13, 5.6.8, 6.0.5, or 6.2.0 and above. They were additionally asked to perform an organization-wide password reset.

The security firm also suggested its customers to implement multi-factor authentication to mitigate the credential abuse threats.
The data breach confirmation from Fortinet comes hot on the heels of the credential abuse disclosure by the threat actors. The hackers leaked a list of FortiGate VPN SSL credentials for free on a new Russian-based hackers’ forum called RAMP. They also put the credentials for sale on the Groove ransomware data leak site.
Also Read: AT&T Purportedly Breached! 70 Million Users’ Data Compromised
Fortnite Data Leak on Groove Hacking Forum
According to Advanced Intel, the leaked list contained 799 directories and 86,941 purportedly compromised VPN connections. It also contained raw access to top companies spanning across 74 nations, with India, Taiwan, Italy, France, and Israel topping the list.
“2,959 out of 22,500 victims are US entities,” revealed the researchers.
Geographical Distribution Leaked Fortnite Servers
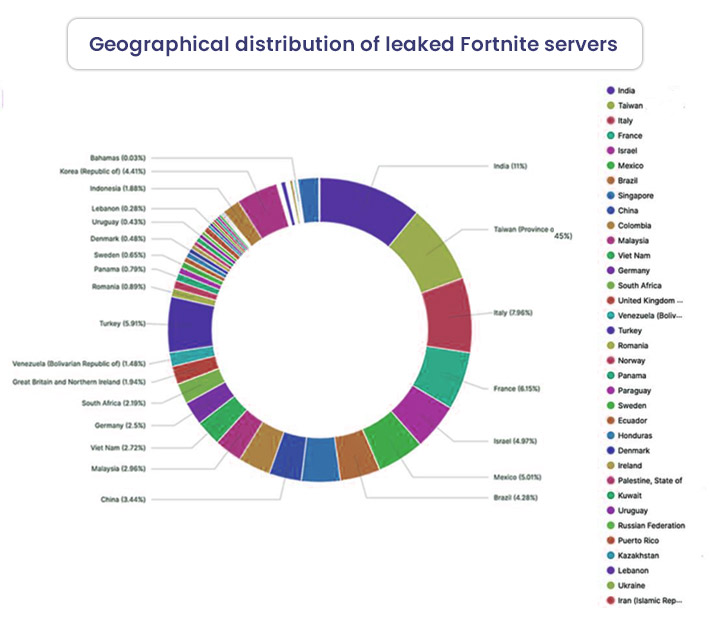
Though Fortnite ascertained the impact to just 87,000 users, Bleeping Computer revealed that the file contained VPN credentials for 498,908 users over 12,856 devices.
The researchers consider the leak extremely severe as the VPN credentials could enable cybercriminals to wreak havoc based on their whims and fantasies.
Also Read: T-Mobile Hack Exposes Personal Data of 47 Million Customers!
However, it is obscure as to why the hackers published the credentials rather than exploiting them for their personal benefits. The researchers believe that the hackers did so to promote the RAMP and Groove hacking forums.
“We believe with high confidence the VPN SSL leak was likely accomplished to promote the new RAMP ransomware forum offering a “freebie” for wannabe ransomware operators,” said Advanced Intel CTO Vitali Kremez.
Though patching is one of the simplest cybersecurity controls, it remains the most disdained security strategy. A recent study by Ponemon revealed that unpatched known vulnerabilities are responsible for 60% of data breaches.
More News Articles:
- Accenture Suffers Ransomware Attack; USD 50 Million Ransom Demanded
- Poly Network Suffers Major Crypto Heist, Hackers Haul Away USD 600 Million!
- PwnedPiper PTS Security Vulnerabilities Put 80% of American Hospitals at Risk!
- Hackers Exploit Synnex to Access Customer Apps on Azure!
- World’s Largest Meat Company Ends Up Losing USD 11Mn Due to Ransom Attack!
- Kaseya Ransomware Attack: Hackers Demand USD 70 Million in One of the Largest Cyberattacks!
- A Single Password Forces Largest US Pipeline to Knees, Prompts Payment of $4.4Mn Ransom!

