IKEA Suffers Reply-chain Phishing Attack, Same as Microsoft Exchange Server Hack!
Cybercriminals are leveraging innovative attack tactics to cripple the cyberworld. Instead of the notorious phishing and spear-phishing attack techniques, the malicious actors are now leveraging a more sophisticated technique known as a ‘reply chain attack.’ While the former techniques imitated the legitimate sender with a forged address, the latter hijacked email chains to insert a phishing email into an existing email thread. The new technique is also known as ‘hijacked email reply chain,’ and ‘thread hijack spamming.’
As the reply-chain emails are legitimate emails from a company and are sent from compromised email accounts and internal servers, the employees are more likely to open the malicious documents.
The latest enterprise that fell victim to this attack vector is IKEA. The perpetuators pilfered the internal reply chain emails to attack IKEA employees with an internal phishing campaign.
Also Read: Online Shoppers at Risk of Losing over USD 53 Million During 2021 Holiday Season!
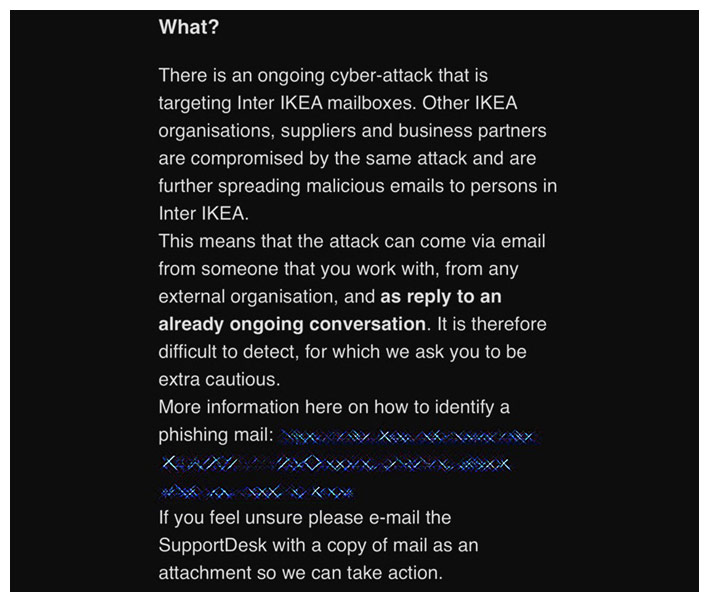
“There is an ongoing cyber-attack that is targeting Inter IKEA mailboxes. Other IKEA organizations, suppliers, and business partners are compromised by the same attack and are further spreading malicious emails to persons in Inter IKEA,” said IKEA in an internal mail to its employees.
“This means that the attack can come via email from someone that you work with, from any external organization, and as a reply to an already ongoing conversations. It is therefore difficult to detect, for which we ask you to be extra cautious,” warned IKEA.
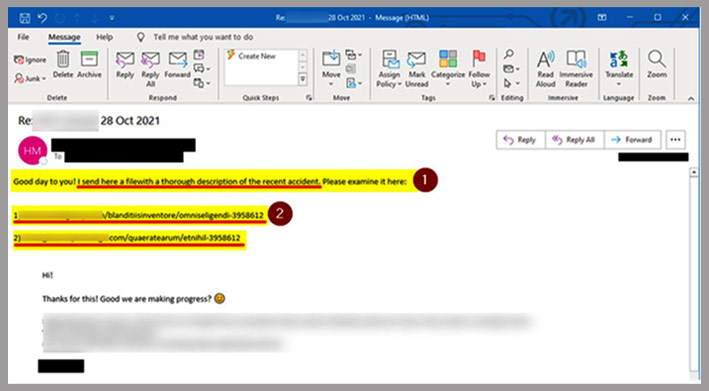
The company informed its employees that the reply chain phishing emails come with links that end with seven digits. It also shared an example of a reply chain email to educate the employees. Moreover, IKEA instructed its employees not to open the emails, regardless of who the sender is.
“If you feel unsure, please e-mail the supportDesk with a copy of mail as an attachment so we can take action,” said IKEA to the employees.
IKEA is also concerned that the employees may unwittingly release phishing emails from quarantine, assuming that the email filter quarantined them by mistake. Amid this concern, the leading furniture retailer had locked the employees from releasing emails until the attack is resolved.
Also Read: People Hacking their Peloton Fitness Equip to Watch Netflix!
“Our email filters can identify some of the malicious emails and quarantine them. Due to that, the email could be a reply to an ongoing conversation, it’s easy to think that the email filter made a mistake and release the email from quarantine. We are therefore until further notice disabling the possibility for everyone to release emails from quarantine,” communicated IKEA to its employees.
Malicious Emails Mask Qbot and Emotet Trojans
When the malicious email is opened, the employees are directed to download a zip file called ‘charts.zip’ that contains a malicious Excel document. This attachment asks the user to ‘Enable Content’ or ‘Enable Editing’ for opening the doc, as shown below.

Once the recipient does so, the malicious macros will be executed that download files named ‘besta.ocx,’ ‘bestb.ocx,’ and ‘bestc.ocx’ on the compromised system. These OCX files are programmed to install a malware payload that includes Qbot and Emotet Trojans.
These trojans lead to further network compromise and ultimately the deployment of ransomware on a breached system.
Also Read: GoDaddy Security Breach: 1.2 Mn WordPress Users’ Data Exposed!
Weighing the severity of the breach, IKEA is considering this incident as a potential cyberattack that could lead to a far more disruptive attack.
The reply-chain hack on IKEA and Microsoft Exchange Server underscores how employee cyber hygiene plays a prominent role in preventing an attack. With cybercriminals continuously honing their tactics, organizations ought to educate their employees on the latest cybersecurity trends and practices. One can reach out to managed security service providers like StealthLabs to stay abreast of the evolving cyber world.
Based out of Texas, StealthLabs has over a decade-long experience in catering to the needs of the cybersecurity industry. Whether you are a newbie or a Fortune 500 company, we have the right expertise to help you address your security needs. With our elite team of security experts at your disposal, you can run your business seamlessly – and more important – securely. Join forces with us to stay cyber resilient and relevant.
More News:
- Hackers Exploit BQE Software to Hit a US Engineering Comp
- Cybercriminals Leveraging Telegram Bots to Bypass MFA and OTP
- DeFi Firm Cream Finance Suffers Crypto Hack,
- Robinhood Suffers Yet Another Massive Breach
- 80% of Organizations Plan to Adopt Zero-Trust Security Strategy!
- REvil’s Faux Pas Thwarts Massive Ransomware Attack

