Zero Trust security strategy has been on top of security leaders’ priority list for many years. However, it’s only been during the pandemic that the ‘Never Trust, Always Verify’ approach has started to catch up.
The upsurge in sophisticated cyberattacks amid the crisis has given the much-needed push for organizations to make this once theoretical model a reality.
According to the 2021 Zero Trust Market Dynamics Survey by Ericom Software, 80% of organizations have hammered out plans to embrace a Zero Trust security strategy within the following year.
Also Read: IT Company Discovers New, Startling Vulnerabilities in Azure
Over 46% of the surveyed organizations are planning to enable Zero Trust security during 2021. Less than 20% of respondents said it would take more than 12 months to implement.
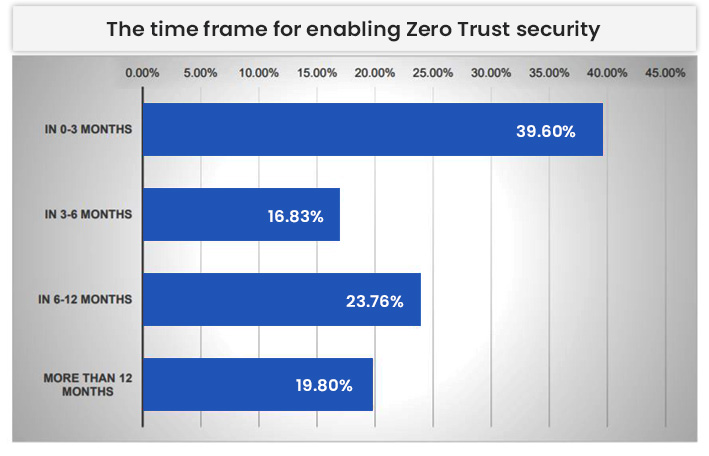
“I was pleased to see the survey results reported significant market momentum around the Zero Trust security framework and am excited about its ability to make a real difference in the security posture of the organizations that adopt it,” said Dr. Cunningham, Ericom’s Chief Strategy Officer.
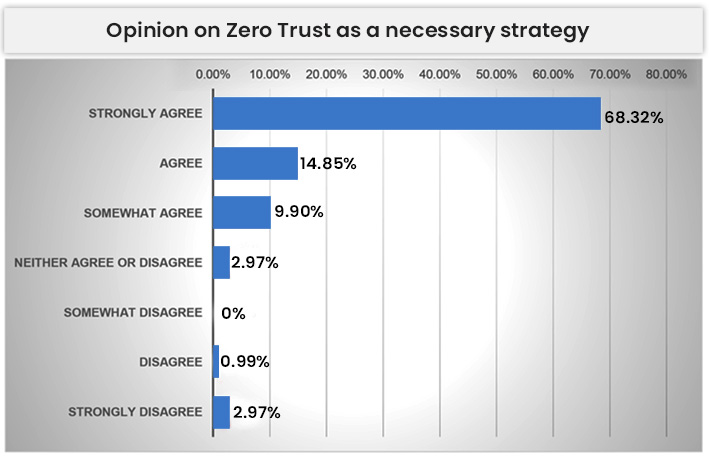
Among the 1300 security and risk professionals who took part in the July 2021 survey, 83% agreed that their company considered Zero-Trust as an essential security strategy.
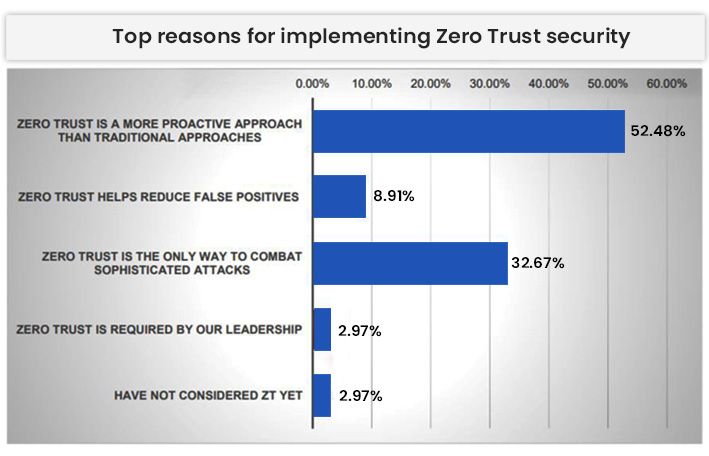
When asked about the top reason for implementing Zero Trust security, over 52% said that the security approach is a proactive strategy, better at axing risk and controlling the threat space. More than 32% of the respondents believed that Zero Trust is the best strategy to ward off sophisticated attacks.
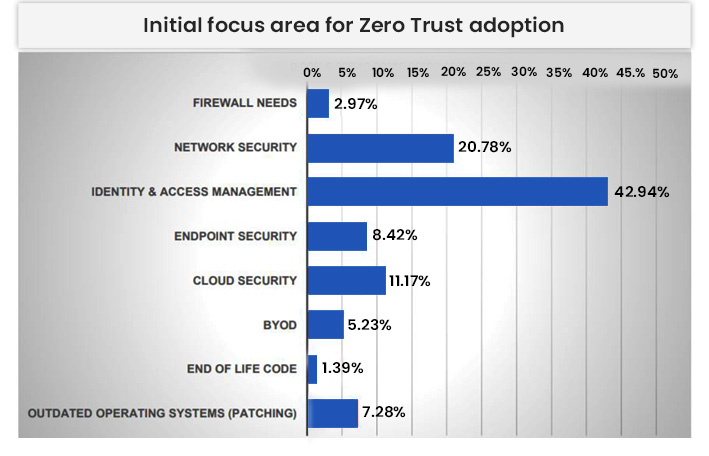
The highest priority area of focus for respondents’ ZT security implementation is Identity and Access Management (42.94%), followed by Network Security (20.78%) and Cloud Security (11.17%).
Despite the fact that 83% of respondents agree that ZT is necessary, almost half of the security professionals (44%) are still prioritizing other security strategies.
According to the survey, 28.05% of organizations would see a delay in ZT initiatives due to budget restrictions. From the IT perspective, 28.27% of respondents identified legacy technologies as significant technical barriers for adopting Zero Trust security.
Also Read: REvil’s Faux Pas Thwarts Massive Ransomware Attack
Lack of expertise, difficulty in change management, and the dynamic nature of business and development are among the most significant technical hindrances for enabling Zero Trust.
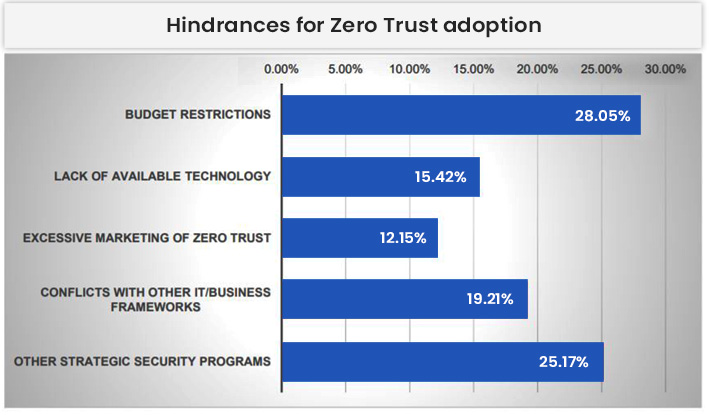
The complexity associated with defining and implementing Zero Trust security policies is considered the most challenging part of ZT adoption by 30.37% of security leaders.
“Zero-trust IT as a concept has, of course, been around for decades. The challenge has always been finding a way to implement it in a way that didn’t result in end users trying to circumvent policies in the name of individual productivity,” noted Cunningham.
Considering the intricacy of the Zero Trust security strategy, over 70% of respondents feel that partnering with a security vendor would speed up ZT implementation. They agree that third-party security service providers help ensure Zero Trust is implemented effectively and initiated in the most essential areas.
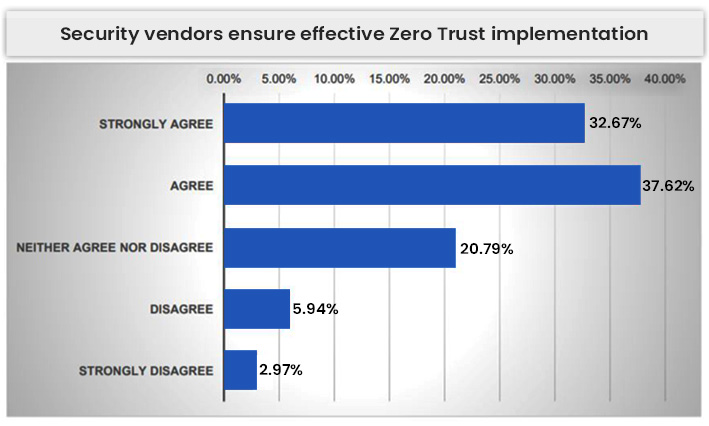
“Security vendors that can help organizations address their pain points around budget, complexity, and flexibility will be in a strong position to partner with businesses as they implement their Zero Trust programs,” said Dr. Cunningham.
“It’s unclear just how great the desire to embrace zero-trust approaches to IT really is versus the actual capabilities of an organization. Cybersecurity expertise, after all, is still difficult to find and retain. However, in the wake of a series of high-profile breaches, it appears the security alarm that has been blaring regularly for years is finally being heard. The issue now is finding a way to respond that doesn’t break the IT budget,” he added.
More News:
- LockBit Hackers Exploit Accenture to Compromises an Airliner!
- User Misconfigurations in Microsoft Power Apps Exposes 38 Million Records!
- Security Firm Fortinet Suffers Cyberattack, Almost 500,000 VPN Account Credentials Leaked
- AT&T Purportedly Breached! 70 Million Users’ Data Compromised
- T-Mobile Hack Exposes Personal Data of 47 Million Customers!
- Accenture Suffers Ransomware Attack; USD 50 Million Ransom Demanded
- Kaseya Ransomware Attack: Hackers Demand USD 70 Million in One of the Largest Cyberattacks!
- World’s Largest Meat Company Ends Up Losing USD 11Mn Due to Ransom Attack!

