The demand for secure access has skyrocketed in recent years.
The businesses should meet the access demands of a diverse landscape of users across numerous, disparate applications while ensuring adequate cybersecurity.
However, slight mismanagement of the user credentials may lead to unprecedented security threats.
According to a recent Verizon Data Breach Report, 81% of the confirmed data breaches involved leveraging weak, stolen and default user passwords.
Whether it is passwords or email addresses, user information can quickly become a complex issue to track without a proper control system.
With the enormous amount of data to be stored, processed and transmitted, many scenarios that require modifications to access permissions arise daily.
Meeting these demands across a wide variety of on-premise and cloud applications requires reliable and flexible access control solutions.
This is where Identity and Access Management (IAM) comes into play.
Defining Identity and Access Management (IAM)

IAM consists of processes, policies, and systems that manage the users’ digital identities in a secure, streamlined manner.
It encompasses various technologies such as Single Sign-On (SSO), profile management, Multi-Factor Authentication (MFA), and password management.
Identity and access management incorporates three significant concepts, identification, authentication and authorization, which collectively ensure that the right users have the proper access.
Thus, IAM solutions have become a crucial component of IT security.
According to a recent survey by KPMG, 92% of businesses plan to increase their investments in identity and access management tools in the coming years.
IAM solutions are beneficial not only for users and security admins but also for enterprises as a whole.
While an effective IAM solution helps enterprises secure efficient access to technology resources across diverse systems, it also delivers many essential benefits.
ALSO READ: Why Do You Need to Opt For Identity and Access Management Services?
6 Key Benefits of Identity and Access Management (IAM)
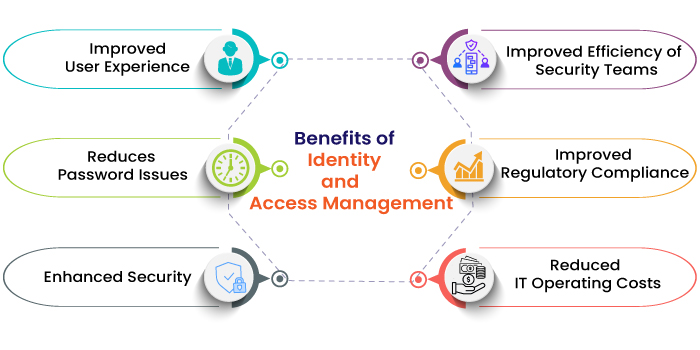
1) Improved User Experience
With the implementation of IAM tools, IT admins can create a unique digital identity for every user that includes a set of credentials. This eliminates the herculean task of the users to manage dozens of accounts for various corporate applications or resources.
With IAM systems, the end-users can access corporate networks, regardless of location, time and device.
Moreover, the SSO method enables the users to access cloud-based, SaaS, web-based and virtual applications with their unique identity.
2) Reduces Password Issues
Apart from enabling easier sign-in processes, IAM solutions prevent many password related issues such as managing passwords in excel or on sticky notes and forgetting user credentials.
The IAM tools offer password management features that help security admins implement password best practices, such as frequent password updates and strong authentication measures including MFA, biometrics, or role-based access.
3) Enhanced Security
IAM solutions help businesses implement adequate security policies across all systems, platforms, applications, and devices. This makes it easier to identify security violations, remove inappropriate access privileges and revoke access whenever needed.
With IAM systems, employees can access the systems depending on their specific role and cannot escalate privileges without approval or a role change. This, in turn, significantly limits the potential insider security threats.
4) Improved Efficiency of Security Teams
Apart from improving the security posture, the most significant benefit of IAM is improving the efficiency and effectiveness of security teams.
With the help of IAM tools, the security admins can grant access rights based on the principle of least privilege to user roles. This ensures that users, including clients, employees, contractors, third-party vendors, and partners, can be quickly and efficiently organized with only the right access.
Moreover, IAM systems use automation, AI and machine learning that help administrators to automate many critical aspects of managing identities, authentication and authorization.
5) Improved Regulatory Compliance
Government data regulations such as CCPA, HIPAA and GDPR make organizations accountable for controlling access to customer and employee information. The regulations have data security, privacy and protection mandates such as who has access to the information and how the access is protected, which are directly related to IAM. Thus, IAM solutions help enterprises meet regulatory compliance and industry best security practice standards.
6) Reduced IT Operating Costs
According to a recent survey, 30-50% of help desk calls are for password resets. And, on an average, a password reset costs an organization around USD 70.
IAM solutions help the organization save these costs by minimizing the time needed to deal with user account related issues.
ALSO READ – Infographic: Top-9 Reasons To Consider IAM Solutions and Services
In Conclusion
With the increasing complexity of data breaches, the scope and scale of identity and access management will continue to witness steady growth.
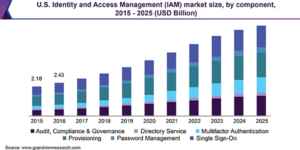
As per the market report by Grand View Research, the IAM market is estimated to reach USD 24.12 billion by 2025, at a CAGR of 13.1%.
Wait No More! Implement IAM Solutions Now!
Need Support? Contact Stealthlabs!
Stealthlabs is a US-based Identity Management (IDM) Service Provider with strong domain expertise and excellence in approach. Our portfolio of IDM services includes Access Management, Identity Governance and Data Governance.

