The global digital landscape is evolving and is becoming more and more customer-centric.
Businesses are now striving to deliver seamless, omnichannel access to customers, support mobile engagements, and roll out personalized consumer applications. Besides, businesses must protect customers’ privacy across a growing number of digital touchpoints while enabling secure, frictionless, on-demand interactions with their brand.
To successfully deliver these experiences, organizations must embrace Consumer Identity and Access Management (CIAM) that offers better customer experiences while protecting and securing customer data and privacy.
What is CIAM?
Customer Identity and Access Management (CIAM) is a framework of business processes, policies, and technologies that enables organizations to manage customer identities’ authentication and authorization.
CIAM is a crucial aspect of customer-facing applications that require users to register identities and create accounts.
A robust CIAM solution offers a combination of features, including:
- Self-service registration
- Password and consent management
- Profile generation and management
- Authentication and authorization into applications
- Identity repositories
- Reporting and analytics
- APIs and SDKs for mobile apps
- Social identity registration and login
- Single sign-on (SSO)
- Multi-factor authentication (MFA)
- Access management
- Data access governance
Why CIAM is Important?
Customers expect two primary things when they interact with brands. Firstly, they want brands to deliver a seamless, consistent, and silent user experience across multiple devices, channels, locations, and applications. Secondly, they expect businesses to provide more robust online security and privacy protections.
- According to a PwC report, 32% of customers abandon a favorite brand after just one bad experience.
- A 2019 Ping Identity Report revealed that 81% of customers would stop engaging with a brand online following a breach, and 24% would stop all interactions whatsoever.
- 70% of customers are more likely to purchase from a company that follows the highest data privacy and security standards.
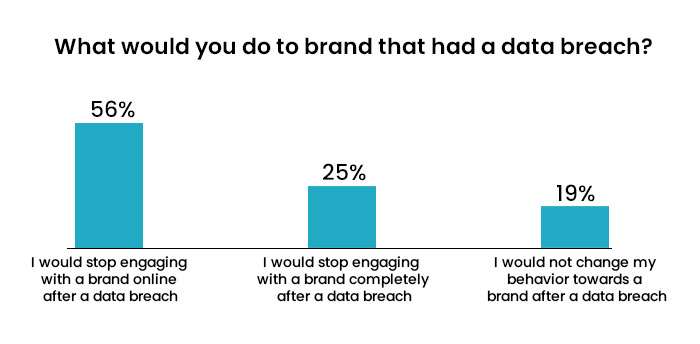
To deliver customers what they want and retain them requires businesses to provide a more personalized experience that protects consumer privacy and enables secure interactions with your brand. CIAM balances both personalization and privacy.
Essential Elements of CIAM?
Organizations require Identity and Access Management (IAM) solutions for a host of end-users, including employees, third-party vendors, stakeholders, and customers. But each class of users demands a different balance of user experience (UX) and privacy. That’s why CIAM features a unique set of elements different from typical identity solutions.
Here are some of the essential features that make a robust CIAM framework:
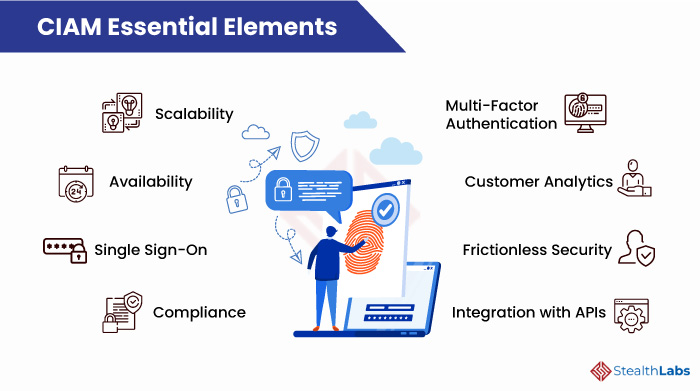
1) Scalability
A robust Customer IAM solution must scale rapidly in response to the high, unprecedented demand from millions and even billions of customers. The CIAM system must handle users across several web and mobile channels while maintaining a high level of performance and a common user experience across these channels.
2) Availability
CIAM framework must offer failover and redundancy mechanisms to ensure that the system is always available. Additionally, it must maintain a high degree of performance and responsiveness to provide frictionless customer access.
3) Single Sign-On
Single Sign-On (SSO) enables users to log in once and automatically access all their applications and services. It eliminates the need to remember many different sets of credentials for each application or service. Thus, it provides a seamless experience for your users when engaging with your applications and services.
4) Multi-Factor Authentication
Multi-Factor Authentication (MFA) ensures only the right user gets access by adding an additional authentication layer to the traditional username/password combination to enhance applications and services’ security. MFA demands an extra credential for customers to prove their identity. That could be an OTP sent to the user’s registered mobile number, email verification, or biometric verification like a fingerprint or face recognition.
5) Customer Analytics
Gaining insights into users can give a major competitive edge, but only if the data is organized, accessible, and accurate. A CIAM solution must integrate Customer Behavior Analytics (CBA) that tracks the customer behavior and enables the organization to evaluate user preferences, buying patterns, and channels customers interact with.
6) Compliance
Ensure that your CIAM platform is compliant with regulatory compliances such as General Data Protection Regulation (GDPR), California Consumer Privacy Act (CCPA), and Health Insurance Portability and Accountability Act (HIPAA). Adherence to regulatory compliance assures customers that their data privacy is protected.
7) Frictionless Security
A robust security framework and roadmap should underpin any Customer IAM initiative. Your CIAM must enable advanced frictionless security while ensuring seamless authentication between users, systems, and devices and optimal customer experience.
8) Integration with APIs
A good CIAM platform must be able to integrate more than just people. It should integrate identity-filled business processes and practices and connect all native and third-party applications that handle customer data. As APIs let you quickly integrate systems that need to work together across providers, your CIAM must integrate seamlessly with APIs.
Business Benefits of CIAM
A modern customer identity and access management solution provides the following benefits for businesses and their customers:
- Improves login and authentication process
- Ensures customer data privacy
- Provides seamless and secure customer experience
- Consolidates various identity stores
IAM Vs. CIAM – Which Solution is Right for You?
Businesses implement an Identity and Access Management (IAM) solution to apply the highest level of security over every security interaction to ensure the proper access to the right resources at the right time.
The challenge with traditional IAM solution applied to the consumer is it lacks the features needed to deliver a great customer experience.
CIAM offers a new, holistic approach to digital identity management compared to traditional IAM solutions.
Here’s a comparison between IAM and CIAM to help you choose the right solution:
| Detail | CIAM | IAM |
| Purpose | Consumer-facing solution that manages customer identities | Employee-facing solution that manages employee identities |
| Authentication | Multiple identity options, such as social login, email login, and phone login | One identity option, i.e., one internal central IT system |
| Scalability | Seamlessly accommodates tens of millions of users | Accommodates 10s to 100,000s of users |
| Data Privacy and Regulations | Customer data handled is subjected to various global privacy and data regulations | Personal data is managed within the organization |
| User Experience | High customer experience and performance | Moderate user experience and performance |
| Integrations | Integrates with CRM, CSM, DMP, analytics, internal IAM, payment solutions, marketing tools, and more | Integrates with HR and ERP systems |
Conclusion
CIAM is imperative for organizations that handle high volumes of external user activity in the contemporary world of ever-evolving digital technologies and associated cyber threats.
CIAM helps you take the next step in assuring your customers’ data privacy while simplifying their online experience across new digital platforms.
StealthLabs As Your CIAM Partner!
StealthLabs offers a comprehensive CIAM service framework that allows organizations to build progressive trust with their customers by supporting the delivery of secure and straightforward omnichannel experiences.
Consumer IAM Security Services
- Access management design and deployment
- PCI compliance advisory
- Zero trust security
- Managed identity detection and response
- Managed identity services
Our CIAM approach includes the client’s current state analysis, current gap assessment, drafting strategy based on gaps identified and implementing CIAM.
More Articles:

