Insider threats often pose risks to business data compared to external attacks. As per the IBM survey in 2019, 31.5% of the cybersecurity occurrences were executed by malicious insiders, and 23.5% from non-malicious insider threats.
According to the Report of the Institute for Critical Infrastructure Technology, in 2018, malicious insider activity stemming from privilege misuse accounted for around 16% of perceived incidents, while the unofficial revelation of information from non-malicious insider activity accounted for around 18% of all occurrences.
Overwhelmed or exhausted workforces constitute to be the prime set of critical infrastructure insider threats, as America’s infrastructure is intensely under-resourced in some areas.
To take an instance, in 2016, there was a projected 1 million critical infrastructure cybersecurity job opportunities, and that number is anticipated to upsurge to 1.5 million by 2019.
However, the positions remain unoccupied as the existing staffs are either incompetent to execute cybersecurity duties or are dedicated elsewhere. As a result, the incapability to fill the positions with competent people inhibits appointing vital personnel or shifting cybersecurity onto overburdened or frail critical infrastructure personnel.
ALSO READ: Hacker Steals 34 Million User Records from 17 Companies
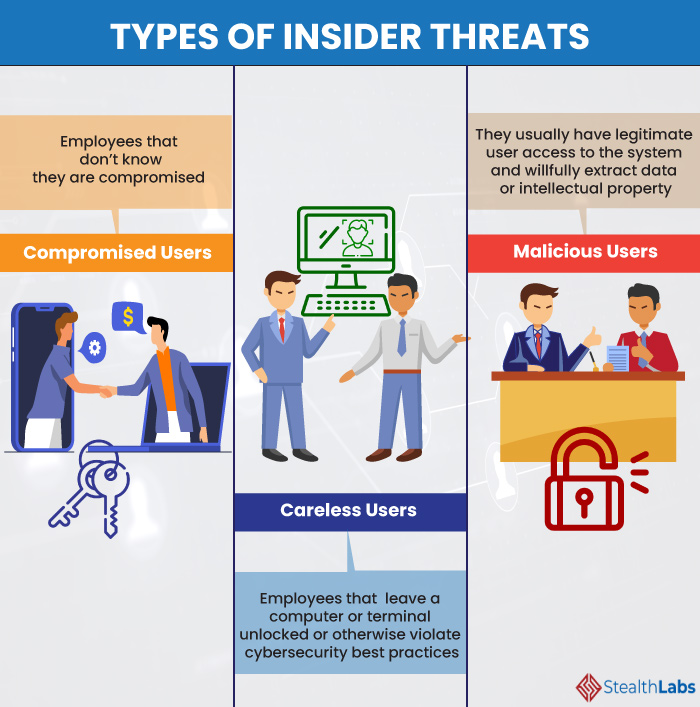
These factors can cause an employee to either intentionally or unintentionally compromise critical enterprise information and assets.
Here are a few tips and techniques to mitigate insider threats:
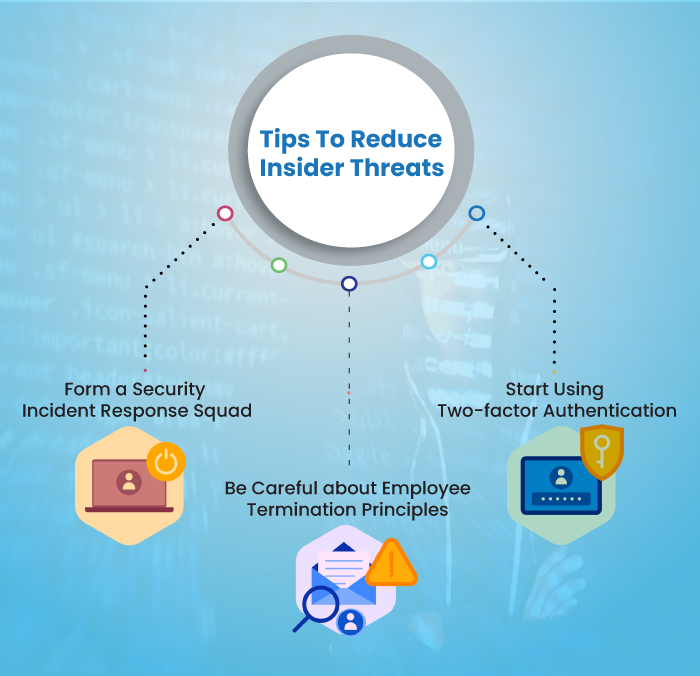
1) Form a Security Incident Response Squad
A dedicated team of experts is indispensable for your security success. This team should be accountable for averting, identifying, and managing incidents and should retain a well-documented plan. Provide your IT staff with the right security training for staying abreast of the latest strategies so that they can easily detect insider threats.
As per the cyber resilience study (IBM 2018), about 77% of the respondents did not have a formal cybersecurity incident response plan. The business leaders should undertake efforts to strengthen the security response team for resolving cyber incidents.
2) Be Careful about Employee Termination Principles
Discard all access and deactivate accounts once your staff resigns. The human resource team and the managers should directly communicate with the IT people when an employee resigns or has a plan of doing so. Several financial companies make the IT staff aware in advance of planned terminations to block the former employees’ access as they are being walked out of the door.
According to a 2017 U.S. State of Cybercrime Survey, about 20% of electronic crime events were suspected or known to be initiated by the insiders.
The human resource team and IT personnel should pay heed to the common sense guide for mitigating insider threats as published in the CMU SEI 2018 Technical Report and should be cautious about the employee termination principles for reducing insider security threats.
3) Start Using Two-factor Authentication
Popular as “something you have and something you know,” one common example is using an RSA token for displaying a rotating series of numbers, comprising an authentication code. Users are required to type a PIN or password, followed by an ever-changing code for accessing a system. This allows anybody to obtain the password or the token (but not both) to be blocked at the gate.
Businesses need to understand the need to take extra steps to avoid threats. Two-factor authentication(2FA) constitutes to be an excellent tool for organizations to defend themselves and their clients. The added security layer goes a long way in helping organizations.
Near about 80% of security breaches can be prevented with 2FA. In fact, security plays a significant role in client purchase decision making.
In Conclusion
Follow these simple tips for reducing insider security threats. Identity and Access Management Solution (IAM) could be an ideal solution as the security of an organization depends on the security of its personnel’s identities. This reduces the frustrations of individuals involved in the process of automating cyber-hygiene.
Without IAM services, several users are swamped by the excess of software-as-a-service credentials and privileged account credentials that they have to remember every day. Opt for the IAM potential of your business from StealthLabs IAM Solutions and secure your digital assets.
More Articles:
- How Businesses Can Implement ‘Zero Trust Security’?
- 83% Of Large-scale Enterprises Transformed Their Cybersecurity Due To Pandemic!
- Hacker Steals 34 Million User Records from 17 Companies
- Infographic: Do’s and Don’ts of Cybersecurity Incident Response
- Infographic: Why Do Organizations Need PAM Services?
- Cyber Threat Basics – Types of Threats and Sources of Cybersecurity Threats

