Top 8 Mobile Cybersecurity Threats You Should Know to Protect Your Data!
Mobile phones have become a convenient portal to the online world, enabling us to stay connected while on the move.
Globally, people are accepting a myriad of mobile apps and services that collect rafts of personal data in exchange for personalized services.
However, it is essential to consider the potential risks of the data on your device falling into the wrong hands and, in the case of enterprise data, any reputational or legal implications this may have.
According to GSMA Intelligence, the number of mobile users in the world today was estimated to be around 5.15 billion, therefore it comes as no surprise that mobile is now the focal point of cyberattacks.
With more web traffic now being received on mobile than desktop, cybercriminals are baiting victims with device-centric scams that leverage popular apps. Instead of casting wide nets with comparatively obsolete techniques to exploit someone, attackers have increasingly focused on developing the most effective social engineering techniques to bolster success rates.
With the mobile security threat heightened, securing mobile devices goes beyond simple anti-virus software. Users must improve their mobile security practices.
Here are the eight biggest mobile device cybersecurity threats that help you know how to secure your personal data:
Also Read: Top 15 Cybersecurity Myths Vs Reality
What Are Mobile Cybersecurity Threats?
People often perceive mobile security threats as an all-encompassing threat. But there are different types of mobile security threats to be aware of.
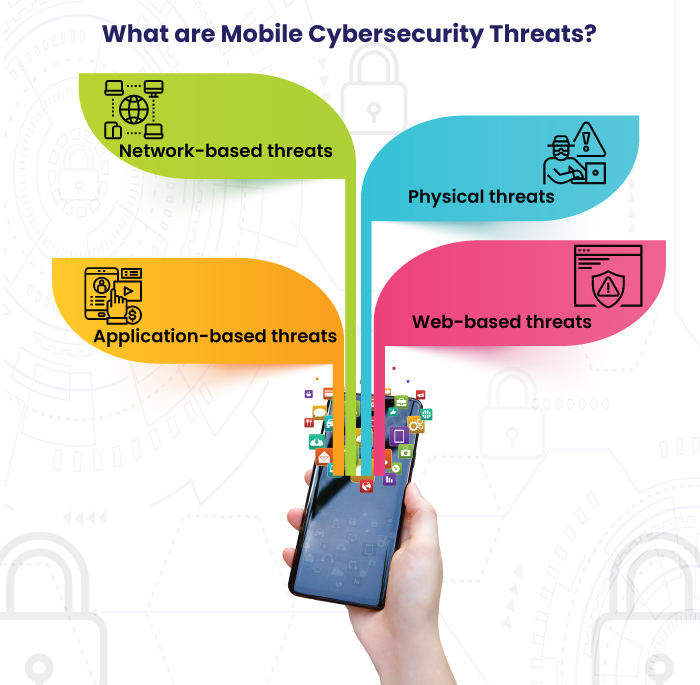
They include:
- Application-based threats occur when you download mobile apps that look legitimate but are specifically designed for committing Spyware and malware are some examples of application-based threats.
- Web-based threats arise when you access a website that looks fine on the front-end, but it downloads malicious content on the device through the back end. Examples of web-based threats are phishing scams and drive-by downloads.
- Network-based threats happen when you access an insecure Wi-Fi network. Wi-Fi sniffing and network exploits are examples of network threats.
- Physical threats occur when you lose your mobile phone or have it stolen. This is the most perilous mobile threat because cybercriminals can get direct access to the sensitive personal information stored on the phone.
Top 8 Mobile Cyber Security Threats
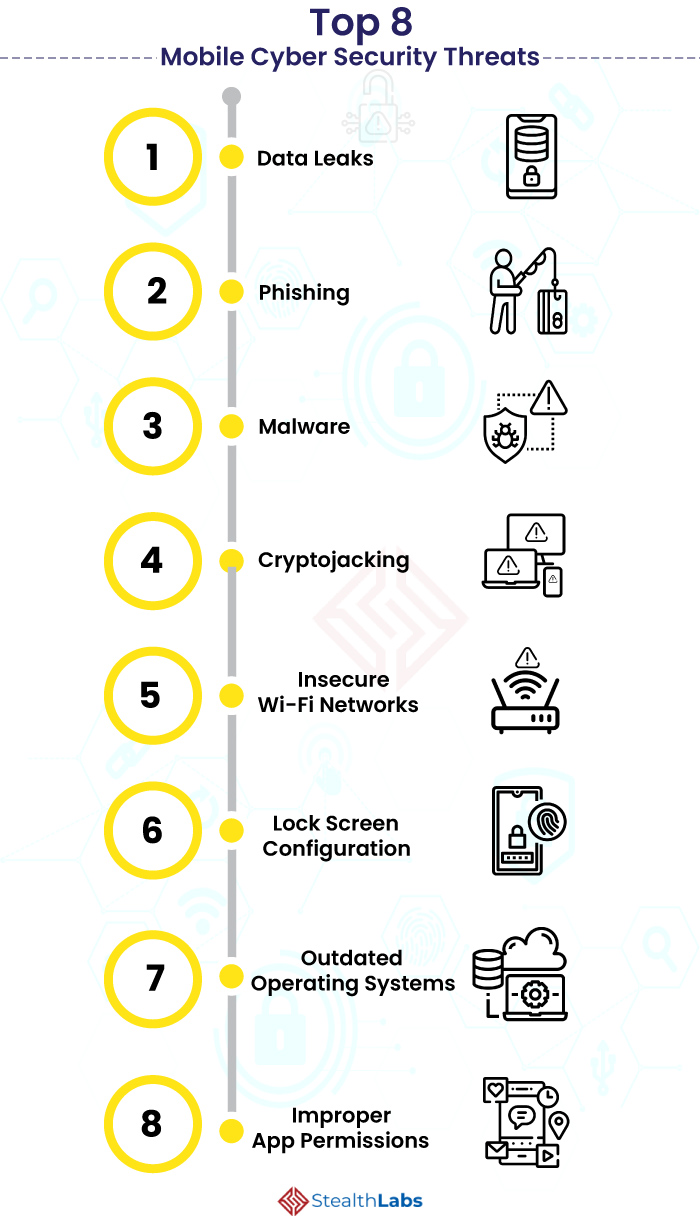
1) Data Leaks
Data leaks are the unintentional or unauthorized transfer of personal information from a mobile phone over the internet. Mobiles apps, malicious or even legitimate, can cause data leakage.
Research shows that the Personally Identifiable Information (PII) is the most frequently leaked in terms of username, password, and credit card numbers/details.
- 77% of mobile users experienced some form of PII leak in 2018
- 90% of mobile data leaks expose a username, 85% expose a password, and 2.3% expose credit card details
News and sports, business, shopping, travel, entertainment, and lifestyle applications are the most highly leaked apps.
To avoid this, the users should give apps the permissions that they absolutely need in order to function properly and should be cautious of the apps that ask for more than necessary.
2) Phishing
Phishing is the most pervasive threat mobile users face today. Mobile users are more vulnerable because they monitor their emails in real-time, opening and reading emails on-the-go. In addition, the smaller screen size makes it challenging to figure out suspicious-looking URLs.
The rate at which mobile users are falling for phishing attacks has increased 85% every year since 2011
To prevent falling for a mobile phishing scam, avoid clicking unfamiliar email links, download apps from trusted app stores, install anti-virus software, and use browsers with security features installed.
3) Malware
Mobile malware has been growing more aggressively since the last few years. There are many categories of malware, including spyware, ransomware, trojan, banker, and adware.
Malicious apps supply malware to mobile devices. These apps exploit OS vulnerabilities to steal data, change the device’s configurations to pull down even more malicious software, deliver pop-up ads or trigger spates of premium SMS messages for monetization, and also cripple devices, for making them unusable for a while.
The number of new mobile malware variants increased by 54% in recent years
To protect your mobile from malware, don’t jailbreak your device, use a VPN, download apps from official stores, use a vulnerability scanner, and encrypt your data.
4) Cryptojacking
Mobile devices have become a lucrative target for cryptoajcking as they possess powerful CPUs and are typically always on. Cryptojacking is highly disruptive to a device as it leads to fast draining of battery, and overheating of the device, slowing down the processor and making it challenging for the user to complete simple, everyday functions.
To prevent cryptojacking, be cautious about phishing emails, unknown attachments, and dubious links, use internet security software, and install ad-blocking or anti-cryptomining extensions on browsers.
5) Insecure Wi-Fi Networks
Wi-Fi hotspots are an enticing attack vector for cybercriminals to extract data from mobile devices. Attackers take advantage of familiar public Wi-Fi names (SSIDs) to trick users into connecting to their imposter networks.
4% of mobile users connect to risky hotspots every week
To prevent this, avoid connecting to free Wi-Fi networks and never use it to access sensitive information.
6) Lock Screen Configuration
Screen lock is one of the most simple and crucial mobile security measures, but surprisingly, many users still don’t use it.
If the mobile phone is lost, stolen, or left unattended, someone can easily access sensitive information, emails, and apps.
52% of people do not password-protect their mobile devices
Creating a robust password-protected lock screen configuration would mitigate the above-said risks.
7) Outdated Operating Systems
Security patches or fixes for operating systems are not installed promptly on mobile devices. By delaying them, users make their mobile devices vulnerable to cyberattacks. Cybercriminals can exploit outdated devices and applications to extract confidential details such as credentials, banking details, and social security numbers.
57% of android devices are running an OS at least two full versions behind the current one
Manufacturers release frequent updates for their OS, containing not only performance improvements but also important security patches for vulnerabilities that may have an active exploit. So, mobile users should promptly upgrade to the latest operating system or application.
8) Improper App Permissions
There are millions of mobile apps available for users, and while some are safe and secure, many are risky. This includes apps downloaded from Google Play and Apple App stores. These apps can be compromised, and sensitive personal data can be shared with third parties.
App permissions play an essential role in determining what functions an app can access on a user’s device. While some app permissions enable app functioning, some present a privacy risk.
45% of the most requested permissions on Android are considered high risk
Thus, mobile users must pay attention to the permissions being granted to apps. Regardless of where these apps are found, there’s always a risk of compromise.
In Conclusion:
As mobile has undoubtedly become the new frontier for cyber threats, mobile users must understand common threat vectors and prepare for the next-gen malicious activities. It’s critical for users to follow standard mobile security practices to minimize the threats.
More Information Security Articles:
- Steps to Create An Information Security Program Plan
- Telemedicine and Cybersecurity: Securing Health Data!
- Infographic – Cybersecurity Myths Vs Reality
- Cybersecurity Myths and Misconceptions Worth Knowing!
- Data Privacy Vs. Data Security: What is the Core Difference?
- 4 Ways MSSPs Can Improve Their Security Offering Through Automation

