Rapid digital transformation, cloud adoption, and distributed workforce have redefined the security perimeter.
As organizations increasingly embrace Bring Your Own Device (BYOD) and Work From Home (WFH) culture, corporate applications and data are migrating from on-premises to hybrid and cloud environments. Now, enterprise data is being accessed and shared outside the corporate networks, bypassing on-premises perimeter-based security models that rely on VPNs and network firewalls.
Thus, the modern security perimeter isn’t defined by the physical locations of the organization, it now extends to every access point that stores, handles, or shares critical corporate information.
Therefore, businesses that rely solely on on-premises security models fail to deliver timely, end-to-end security coverage in the modern, distributed environment.
The present-day security model must effectively adapt to the complexity of the evolving environment, embrace the remote workforce, and secure users, devices, systems, and applications, irrespective of their location. Zero Trust is the answer!
Defining Zero Trust
Zero Trust security model considers each access request as a breach and verifies it as it came from an open network. Irrespective of where the request comes from or what assets it accesses, every access request is thoroughly authenticated, authorized, and scrutinized for anomalies before granting permission. It applies the least privileged access principles to reduce the threat landscape.
Key ‘Zero Trust’ Principles:
a) Verify Thoroughly
b) Grant Least Privileged Access
c) Assume Breach
Building Zero Trust into your Organization
A Zero Trust security model must cover the organization’s entire digital landscape and serve as an Integrated Security Approach (ISA) and end-to-end strategy.
This can be accomplished by enforcing Zero Trust procedures and processes across six key elements, namely, Identities, Data, Devices, Applications, Infrastructure, and Networks.
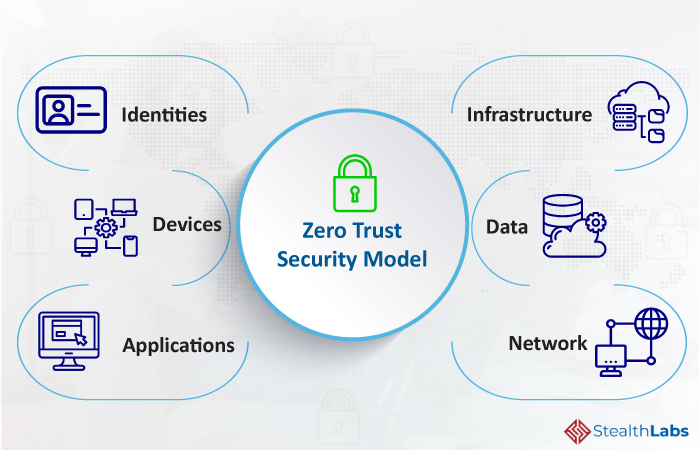
1) Identities
Identities represent users, services, systems, or remote devices. Whenever an identity requests access permission, verify and secure the identity with robust authentication across your digital landscape. Access must be compliant and abide by the least privileged access policy.
2) Devices
Once a user gains access to an enterprise asset, data can transfer to a host of devices, from on-premises workloads to cloud servers and corporate systems to vendor devices. As this distributed data creates a widespread attack surface, organizations must monitor and implement device health and compliance before granting access.
3) Applications
Applications and Application Programming Interfaces (APIs) can be traditional on-premises, modern cloud-native workloads, or SaaS applications. Organizations must enforce controls and technologies to confirm proper in-app permissions, check for anomalous behavior, monitor user actions, and authorize appropriate configuration options.
4) Data
Organizations must shift from perimeter-based data protection to data-driven protection. Use intelligence to categorize, label, and encrypt data and control access based on organizational policies.
5) Infrastructure
IT Infrastructure, including on-premises servers, Virtual Machines (VMs), or containers, are prime targets for cybercrime. Organizations must rely on telemetry to identify attacks and vulnerabilities, automatically restrict and block abnormal behavior, and implement the least privileged access policy.
6) Network
Organizations shouldn’t trust users and devices just because they are on the internal network. Implement network controls to improve visibility and prevent threats from spreading across the network. Employ end-to-end encryption, real-time threat detection, and network micro-segmentation.
In Conclusion
Though a Zero Trust security model is most effective when implemented across the organizational digital ecosystem, it is advised to take a phased approach based on the current cybersecurity maturity, available resources, and business objectives. It’s imperative to consider each investment carefully and align them with the present business needs.
More Articles:
- Zero Trust Security: Why It’s Important for Your Business?
- List of Global Data Breaches and Cyber Attacks in 2020
- Tips to Build an Effective Cyber Incident Response Plan
- Infographic: Do’s and Don’ts of Cybersecurity Incident Response
- Infographic: Why Do Organizations Need PAM Services?
- 6 Steps to Build an Effective Cyber Incident Response Plan
- Privileged Access Management Services: Strategy and Benefits

