Employee data theft is a burgeoning risk for organizations across every industry. While no business can operate successfully without people, human assets can swiftly become a liability.
As data violations arising from employee actions rise in volume, and the associated expense continues to grow, businesses seek ways to control the risk. The clear way ahead is implementing detective, restrictive and responsive steps to decrease the risk of employee data theft.
Ex-employees are known to damage data, steal restrictive software and customer data, and use the company accounts to buy unapproved goods.
The cost of such cyber incidents ranges from $5,000 to $3 million, depending on the organization and the scale of theft.
Employee Theft Statistics

By their nature, electronic reports are transferable, simple to copy, and more likely to theft than paper documents. Today, 97% of all business documents are electronically produced. While analysts regularly discuss the impact this business transformation has on electronic discovery, departing employee data theft implications are just as vital but often neglected.
The purposes why an employee who either resigns or is asked to go carries classified company data vary from being benign and misled to deliberate for personal gain.
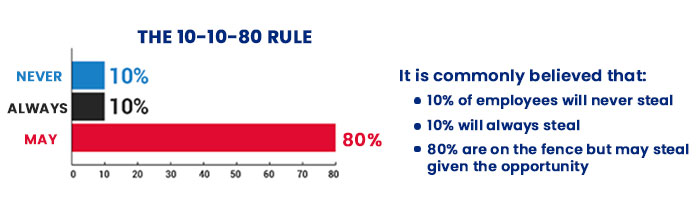
Let us have a sneak-peak into the most reliable methods to stop data theft from departing employees:
1) Policies at Place
The primary layer of protection an employer should have is a comprehensive and well-communicated set of organization policies and systems.
a) The Acceptable Use Policy governs the use of all company assets and safeguards to stop the stealing of classified data and general procedures restricting the copying of data. It governs the use of computer hardware or software, which places company data in danger.
b) The Data Classification and Retention Policy’s objective is to recognize all types of data generated within a company and how long it should retain it.
2) Technology Shifts
The following crucial step in prevention is to station efficient technical solutions to shield your data. In many organizations, a few trivial changes to the IT system can produce meaningful outcomes.
One necessary change is to exclude employees from the Administrator group on their computer. It blocks them from installing any software or hardware. Businesses should also not permit employees to create CDs/DVDs or copy data to USB drives, except for a business necessity.
3) Forensics
While procedures and technology will limit casual data theft, committed employees will still steal data. If this occurs, defend your business by establishing two things; the exiting/departing employee took data without your consent and that the stolen information caused damage. Forensics specialists can find and document cases of an employee’s lewd conduct using specific software and hardware techniques.
4) Disabling Access
Finally, disable employee access to software and systems as soon as you receive an approved resignation or termination mail from HR. It restricts possible avenues that the employee might otherwise use to steal data.
Final Thoughts!
Organizations must find more efficient ways to shield their assets. Since the trial is costly, time-consuming, and may not produce the wanted results always. Training ensures that all employees, including executives, have absolute knowledge of company policies and know-how sensitive data should be handled.
More Cybersecurity Articles:

